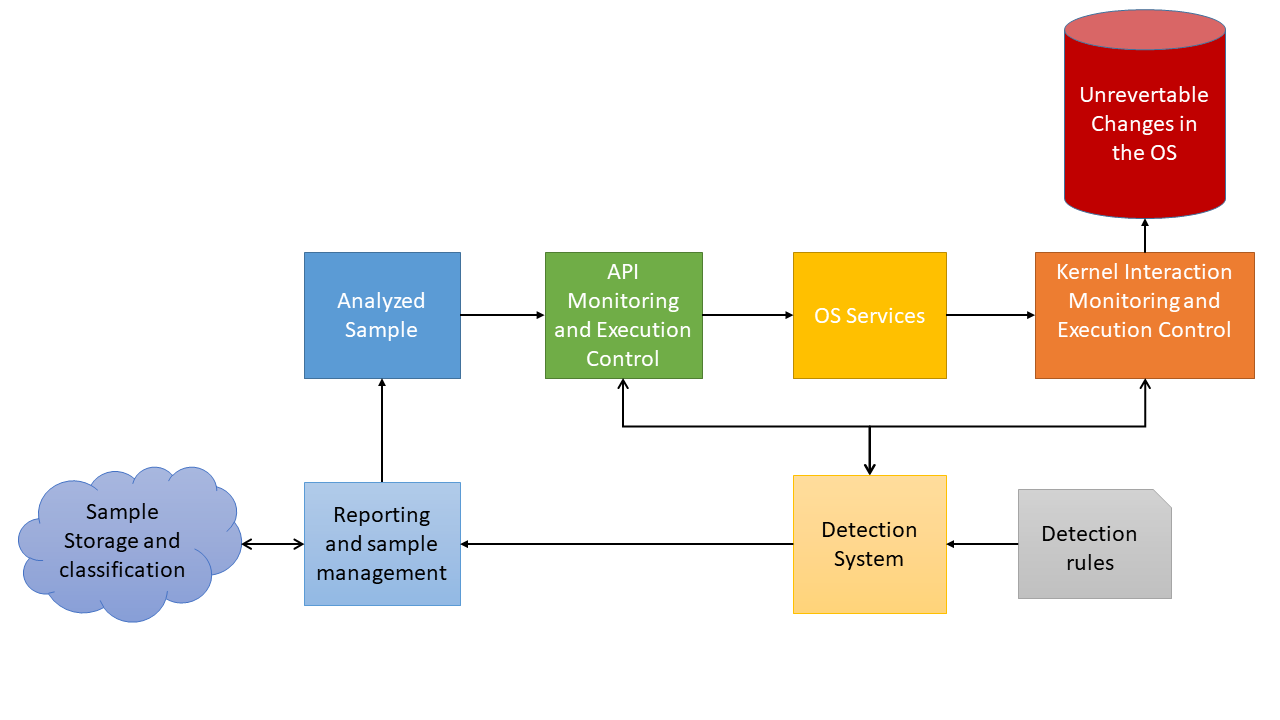
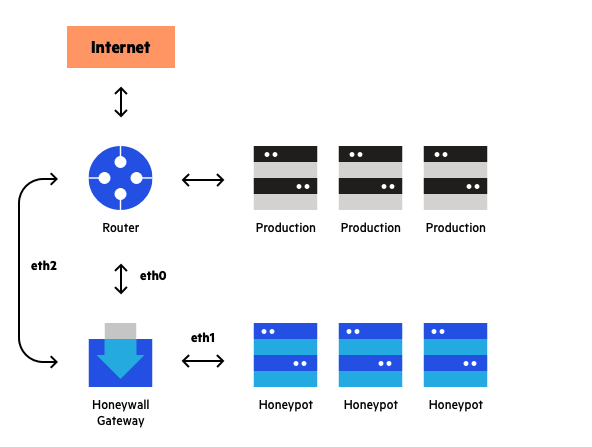
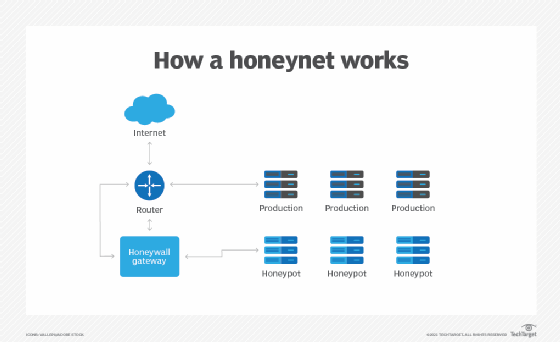
GitHub - rcamino/honeypot-detection: Code for the paper "A Data Science Approach for Honeypot Detection in Ethereum"

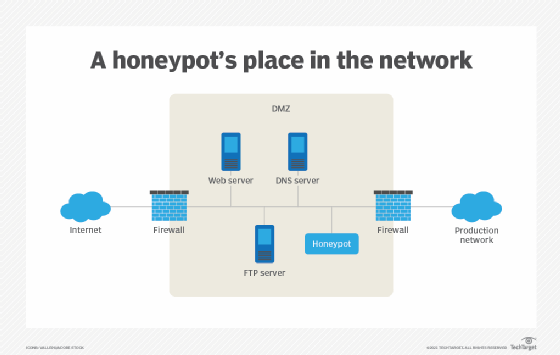
A survey on Intrusion Detection Systems and Honeypot based proactive security mechanisms in VANETs and VANET Cloud - ScienceDirect

![PDF] Overview of Honeypot Security System for E-Banking | Semantic Scholar PDF] Overview of Honeypot Security System for E-Banking | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b28d1ca5b241717abc2f62a515ace34da448843c/3-Figure3-1.png)