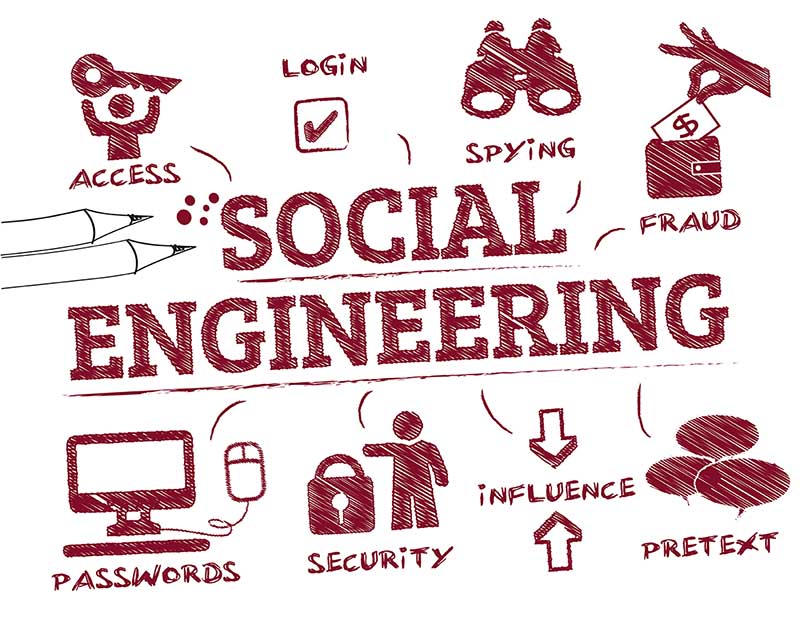
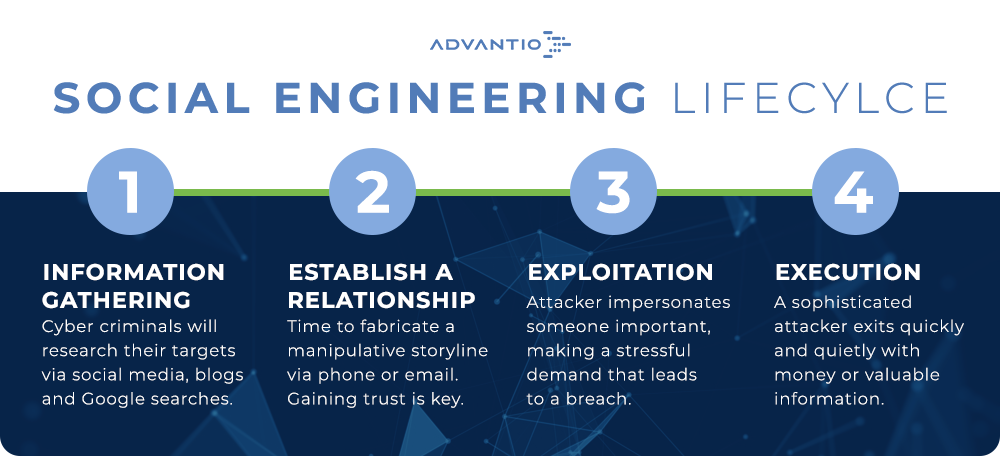
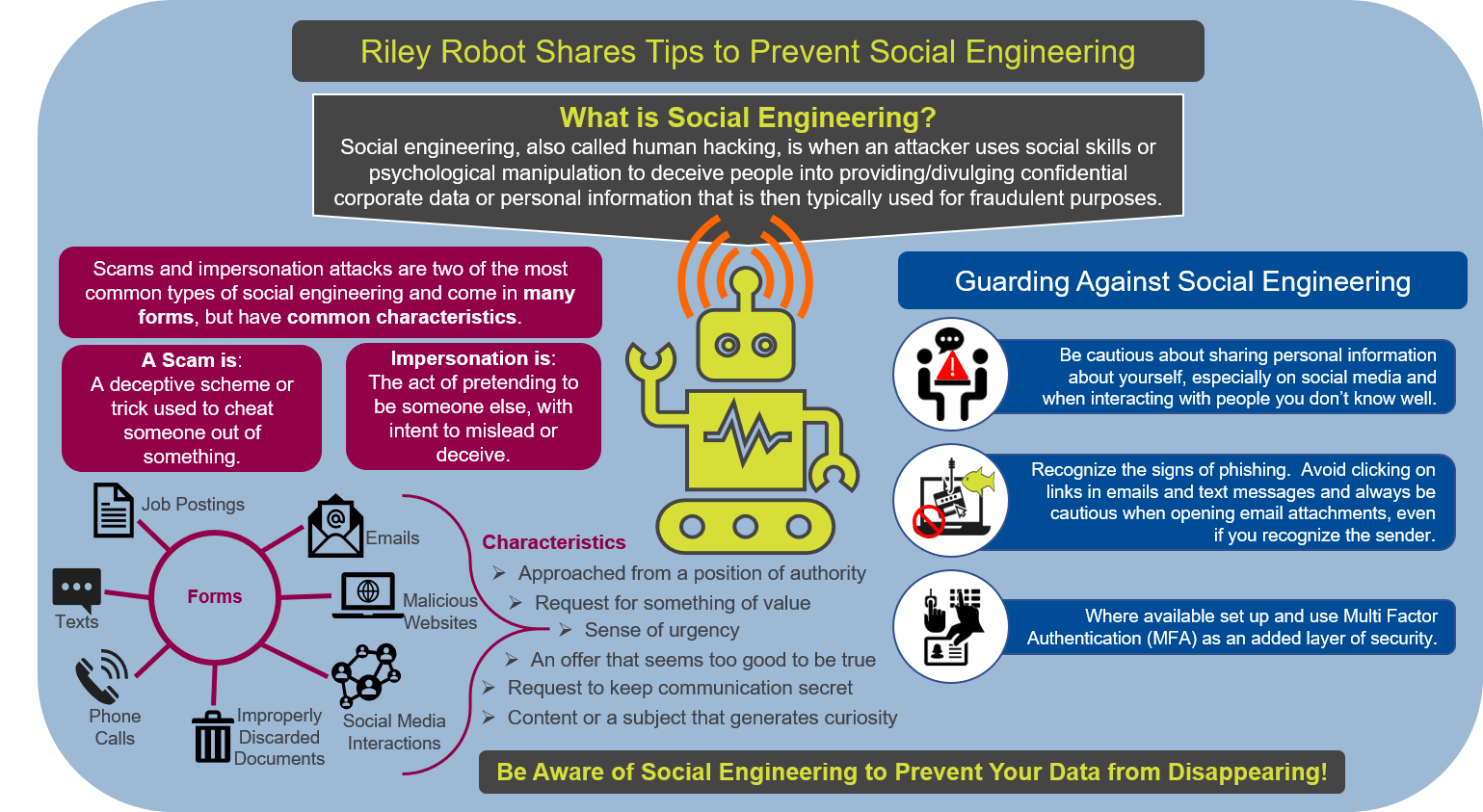
15 Different Types of Social Engineering Techniques Hackers Use to Hack the Victims - The Sec Master

Ilustración de Ilustración Conceptual De Vector Plano Isométrico 3d De Estafas De Phishing De Internet y más Vectores Libres de Derechos de Delito informático - iStock


![23 Social Engineering Attacks Targeting You [INFOGRAPHIC] 23 Social Engineering Attacks Targeting You [INFOGRAPHIC]](https://www.smartfile.com/blog/wp-content/uploads/2016/03/se-digital.jpg)