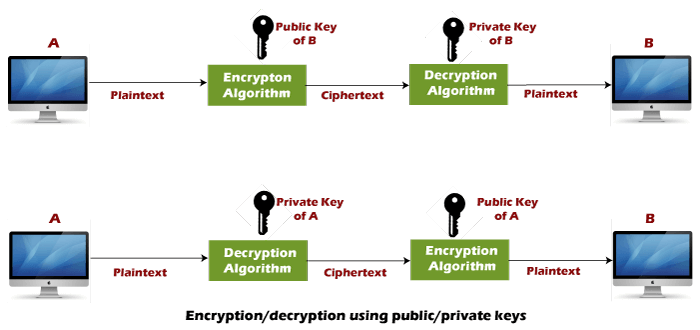
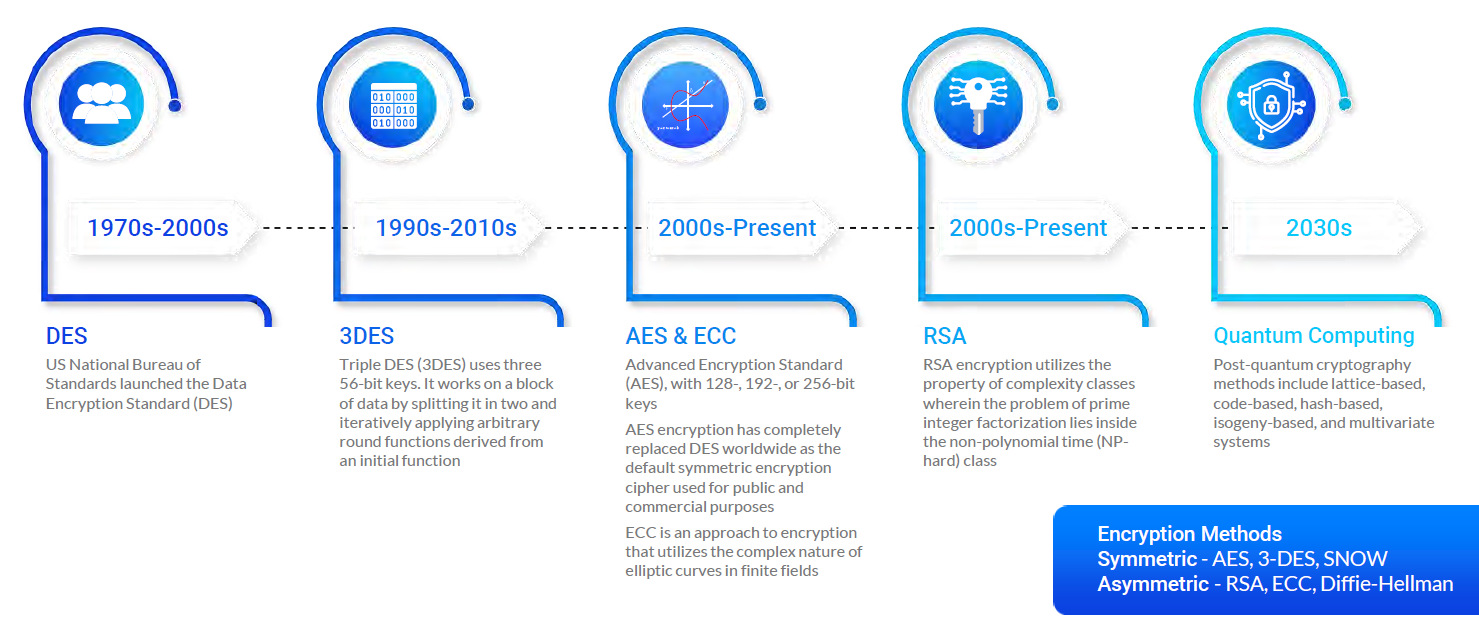
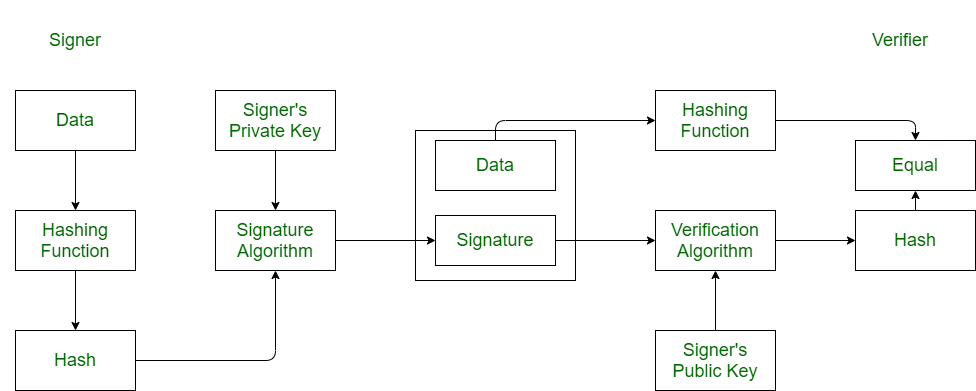
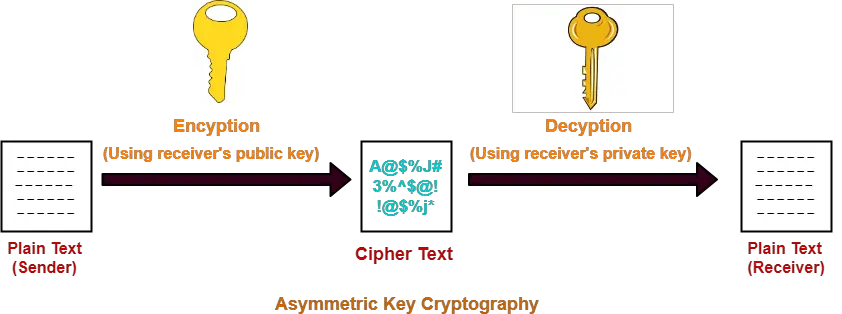
A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention
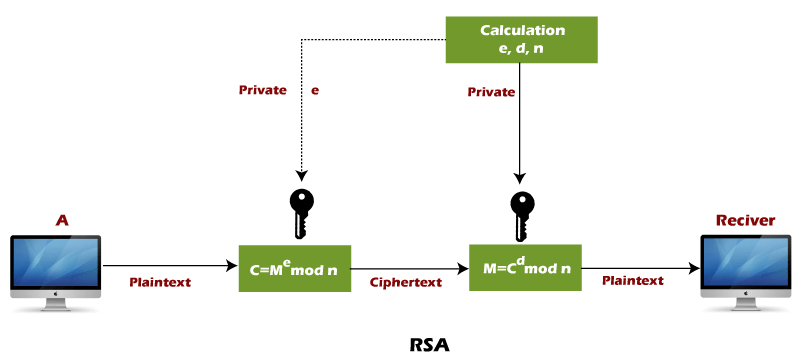
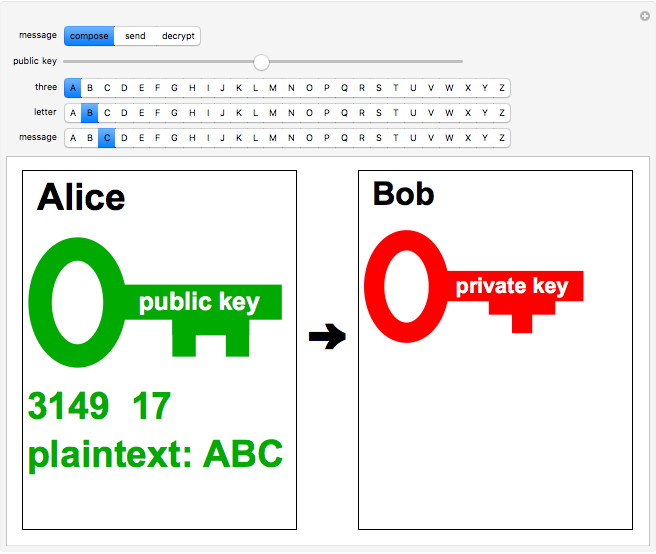
Design and Implementation of Rivest Shamir Adleman's (RSA) Cryptography Algorithm in Text File Data Security
the RSA cryptosystem 1.2 Objective of the Study The objectives of this... | Download Scientific Diagram
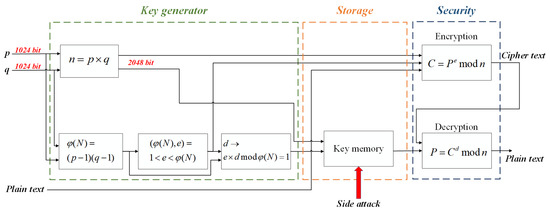
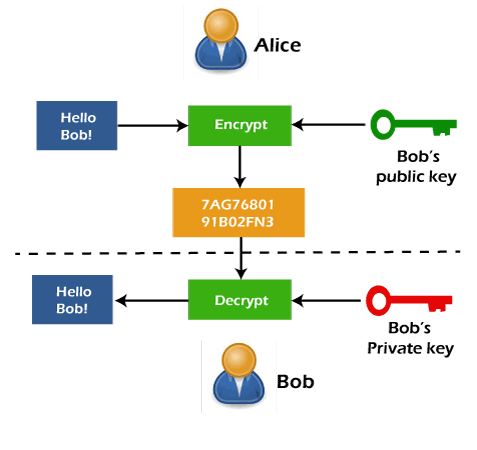
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices