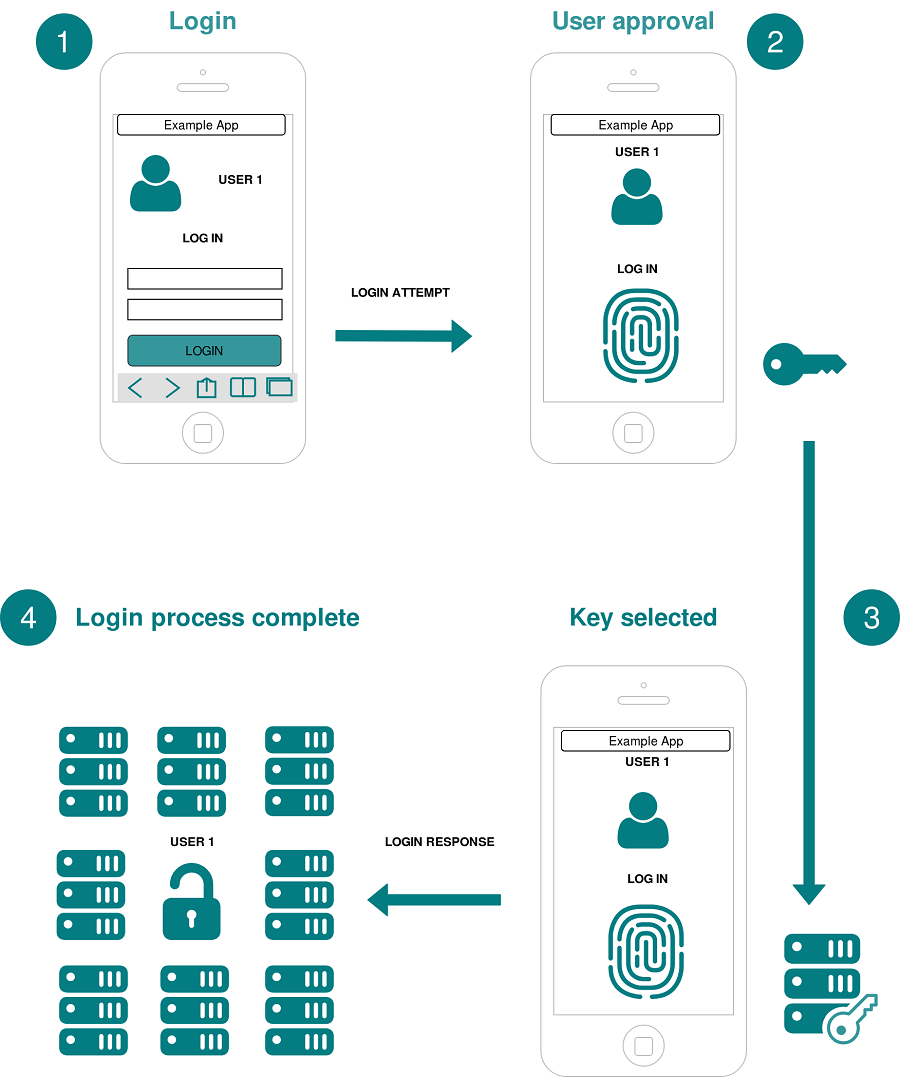
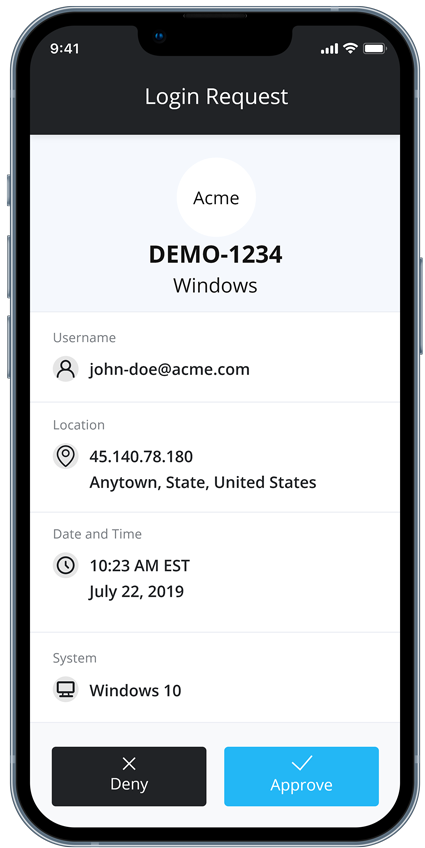
Two step authentication, 2-step Verification SMS code password concept. Smartphone with special 2FA software and tablet pc with multi-factor authentication safety and secure login form foto de Stock | Adobe Stock
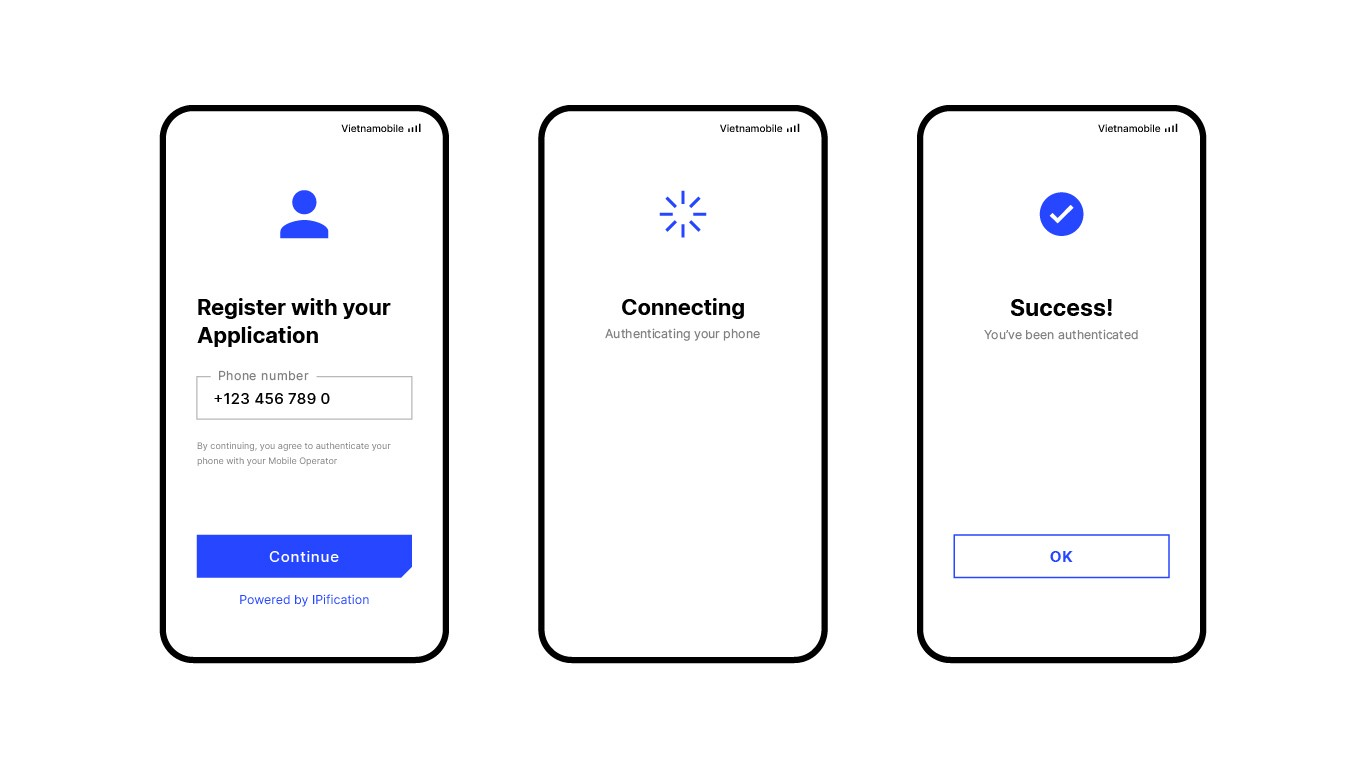
GSMA | Vietnamobile Launches Mobile ID Service - IPification, The Safest and Easiest Authentication Solution Available Today for Online Transactions - 会员资格

Smartphone verification process flat vector illustration, smartphone authentication, online security and protection. Secured information, data privacy icon design for web banners and apps vector de Stock | Adobe Stock

Amazon.co.jp: 3G IP12 PRO+, Cheap Smartphone, Smartphone, Mobile Phone, 6.26 Inch HD+, Large Screen, 1GB RAM + 8GB ROM Mobile Phone, Dual SIM 2MP + 5MP GPS, WIFI, Face Authentication, Fingerprint Authentication,

2fa password login code verification, two step authentication on smartphone vector illustration, flat cellphone and computer safety login or signin, two steps verification via mobile phone and pc vector de Stock
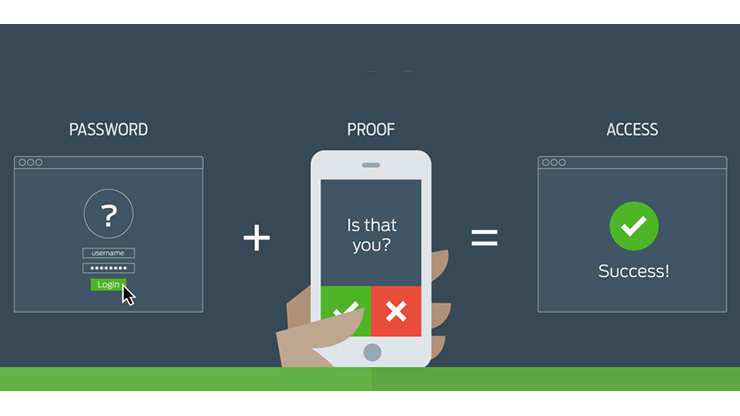
Two factors are better than one: Sign up now for Duo authentication | MIT News | Massachusetts Institute of Technology